Cybersecurity Experts Warn: This is the Largest Credential Exposure Ever Recorded—Here’s How to Protect Yourself
The Largest Credential Breach in History
On June 18, 2025, the cybersecurity world was rocked by the revelation of a record-breaking data leak involving more than 16 billion compromised credentials. Unlike a traditional breach stemming from a single company, this leak resulted from a massive aggregation of stolen data compiled over several years through malware known as infostealers.
The breach, reported by Cybernews, involved 30+ leaked databases—some newly published and others recycled but still shockingly relevant. Cybercriminals used these infostealers to silently extract sensitive data such as:
- Email addresses
- Passwords
- Authentication cookies
- Session tokens
- Autofill data from browsers
These pieces of information were then compiled into what experts are calling a “Super Breach Dataset.”
📉 How Did This Breach Happen?
This leak wasn’t caused by a single hack, phishing scam, or server misconfiguration. Instead, it reflects a long-term trend: users infected with infostealer malware unknowingly surrendered data over time. Once installed, these malicious programs quietly collect everything a user types, views, or stores in their browser.
The data was then exfiltrated and sold on darknet forums or used for targeted attacks.
In short: This wasn’t one break-in—it was millions of invisible thefts stitched into one colossal leak.
🏢 Which Companies Are Affected?
No major corporation has yet confirmed being directly hacked in this event. However, because the stolen credentials came from individual users, virtually every popular platform was included. The exposed data includes login credentials for:
- Google (Gmail, Drive)
- Apple (iCloud, ID)
- Meta (Facebook, Instagram, WhatsApp)
- Microsoft (Outlook, Teams)
- Netflix
- GitHub
- Telegram
- Twitch
- Zoom
- Amazon
Additionally, a significant number of credentials were tied to financial services, government portals, cloud platforms, and corporate tools.
It’s important to emphasize: Just because your provider wasn’t hacked doesn’t mean your data wasn’t stolen.
📂 Why This Data Dump Is Different
Let’s put this breach into perspective.
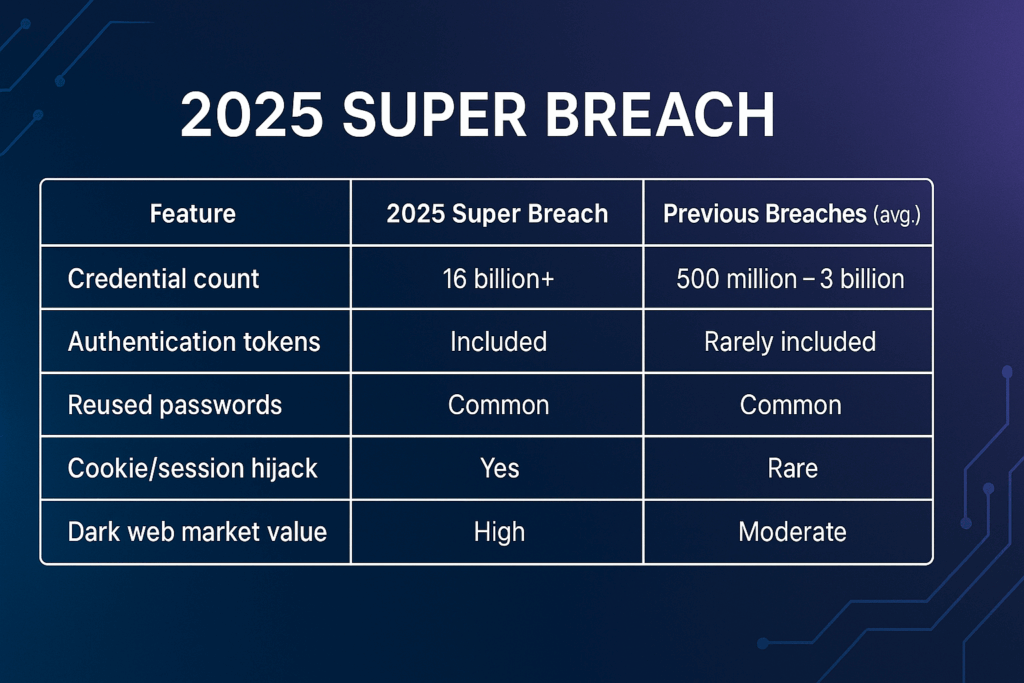
Why is this so alarming?
- Scale: 16 billion credentials is more than twice the number of humans on Earth.
- Freshness: Many credentials were harvested within the last 12 months, meaning they’re still valid.
- Depth: The inclusion of cookies and tokens allows hackers to hijack sessions without needing passwords.
🛠️ What Should You Do Right Now?
Here’s your personal action plan to secure your digital life:
✅ Step 1: Change Your Passwords
Prioritize these:
- Email accounts (especially Gmail, Outlook)
- Cloud services (Apple ID, Google Drive)
- Social media (Facebook, Instagram, LinkedIn)
- Banking or payment apps
Use long, complex, and unique passwords for every site. A password manager like Bitwarden or 1Password can help you manage them.
✅ Step 2: Enable Multi-Factor Authentication (MFA)
Activate MFA for all critical accounts. Prefer app-based authenticators (like Google Authenticator or Authy) over SMS codes, which are vulnerable to SIM-swapping.
✅ Step 3: Adopt Passkeys Where Available
Google and Apple now support passkeys, which are phishing-proof and don’t require passwords. Enable these for:
- Google accounts
- Apple ID
- Microsoft
- Amazon (in beta)
✅ Step 4: Run a Breach Check
Use trusted services to check if your credentials are exposed:
✅ Step 5: Monitor Account Activity
Regularly check your email, bank, and app activity logs for unusual login locations or transactions. Report anything suspicious immediately.
📉 What Are Infostealers and How Do They Work?
Infostealer malware is typically delivered through:
- Infected downloads (pirated software, cracked apps)
- Malicious email attachments
- Fake browser extensions
Once inside your system, they extract:
- Stored credentials
- Autofill data
- Clipboard content
- System metadata
They’re stealthy, quick, and don’t need administrative access to steal your data. Worst of all, users may never realize they’re infected.
📜 A Brief History of Credential Leaks
This event joins a growing list of massive leaks:
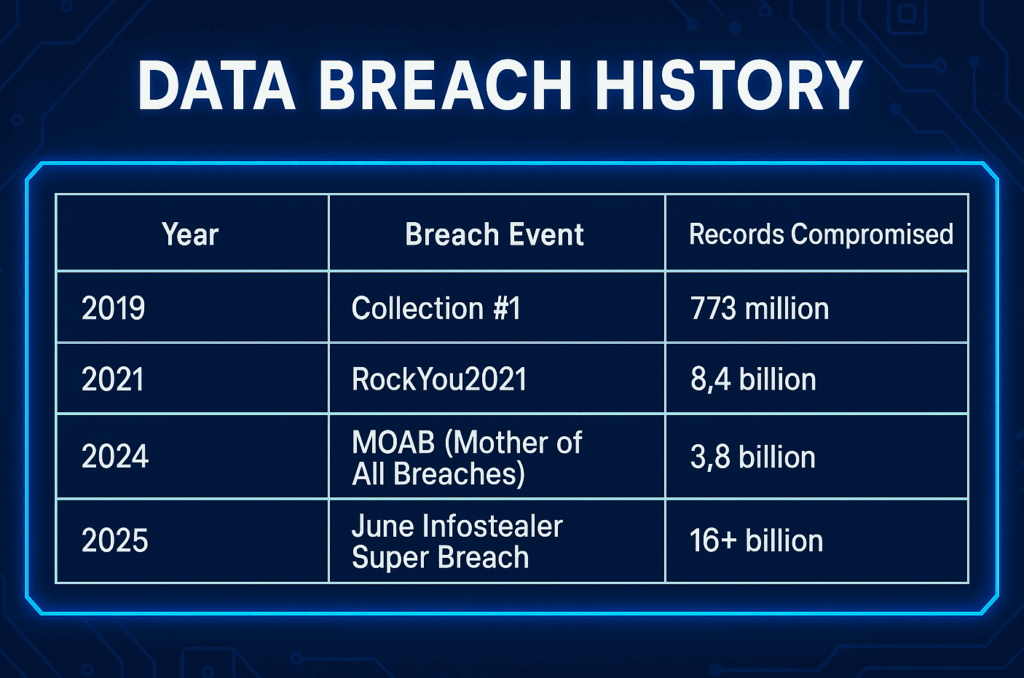
Each new leak grows exponentially and reflects an uncomfortable reality: the internet runs on outdated, password-based systems.
📢 Expert Reactions
“This breach is not just another warning shot. It’s a full-blown alarm bell ringing for everyone who uses the internet.”
– John McAfee Jr., Cybersecurity Analyst
“We’ve built our digital world on a house of cards called passwords.”
– Lena Trujillo, Security Researcher at ZeroDay Labs
🧭 Final Thoughts: The Future of Digital Identity
This breach is a tipping point. The era of relying solely on passwords is officially over. With cybercriminals growing more advanced and infostealers targeting unsuspecting users, it’s time we rethink authentication altogether.
Whether you’re an individual, IT admin, or CEO—action is no longer optional.
